A month or two ago I did set up a handful of new Azure Entra ID tenants for one of my talks. The good thing about this is that I had a few more playgrounds to test things out, and did find out something very interesting. But before we get to that, let’s go back to the beginning.
Creating a new Entra ID tenant
Creating a new Entra ID tenant is very similar to creating another resource in the portal. Use search, make sure you have the right one and click create. Provide the details and you’re done.
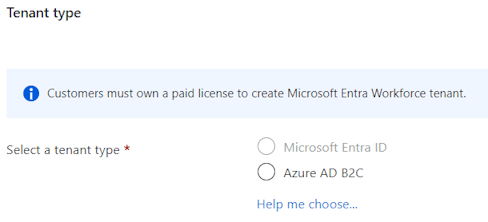
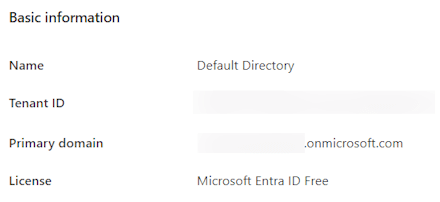
That is … if you have a paid license on your main tenant. Since I’m using my MVP tenant for this, I don’t have a paid license. The same count for anyone setting up a tenant with their MSDN subscription. You can easily check this by looking at your Entra ID properties.
Note: As you can see, you can still create an Azure AD B2C tenant. This allows you to build a B2C SaaS solution without cost up to 50.000 monthly active users. You can read more about this here.
So I had to switch to one of my corporate accounts to create the Entra ID tenants, after which I invited my MVP account as a guest and promoted that account to global admin. This way I can still use my MVP account to manage the tenant during my demos.
The risk
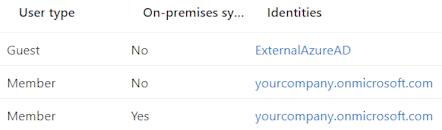
Some of you readers might have spotted the risk already (or even have frowned upon what I did). But let’s take one step back first: in an Entra ID tenant you typically have Member accounts, which are created in the tenant itself. This can be a cloud-only account or a synced account from your on-premises Active Directory.
And then you have Guest accounts, which are accounts from other tenants. These can be Microsoft accounts, or other Entra ID tenants (currently still shown as ExternalAzureAD).
So I decided to give my second account global admin rights, as my primary. What does this role bring?
This is a privileged role. Users with this role have access to all administrative features in Microsoft Entra ID, as well as services that use Microsoft Entra identities like the Microsoft 365 Defender portal, the Microsoft Purview compliance portal, Exchange Online, SharePoint Online, and Skype for Business Online. Global Administrators can view Directory Activity logs. Furthermore, Global Administrators can elevate their access to manage all Azure subscriptions and management groups. This allows Global Administrators to get full access to all Azure resources using the respective Microsoft Entra tenant.
The person creating (and thus ‘owning’) the tenant is automatically assigned this role.
The joke I played on myself
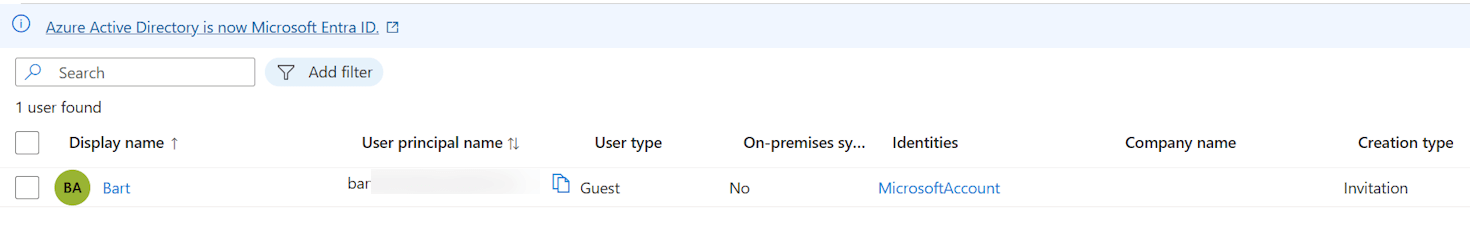
I was cleaning up some test users after the demo using my Guest global admin account and noticed that I could delete the primary admin as well.
Conclusion
Please take some time to let this sink in. I was able to delete the primary admin of the tenant, using a guest account. This is a huge security risk, as I could have deleted the entire tenant.
Next to that, the documentation shows that you can also elevate access to all Azure subscriptions and management groups. This means that I could have deleted all resources in the Azure subscriptions linked to this tenant as well. Or even worse … transfer these subscriptions to another tenant so they are out of reach and start consuming credits. I had to explain this to a CSP recently as they were not aware of these rights (and risks).
So:
- Always review who is asking for admin rights and if they really need these right. Personally I refuse global admin rights in my customer’s tenants if I don’t need them.
- The above statement counts for any privileged role.
- Use PIM to assign these rights for a limited time, and trigger an alert.
- Guest accounts typically don’t need these rights, there are better options for service providers to help you out (like Azure Lighthouse).